No matter where you are in your tech career– from a recent graduate just starting out to a well-established engineering expert and anywhere in between– it’s never a bad time […]


No matter where you are in your tech career– from a recent graduate just starting out to a well-established engineering expert and anywhere in between– it’s never a bad time […]

The COVID-19 pandemic has disrupted the way we work and learn in a short period. Despite the best efforts of K-12 STEM educators to transform their classes into virtual environments, […]

With the emergence of 5G technology, cities all over the world are rapidly transforming, and local governments are scrambling to adjust. David Witkowski, an expert in wireless telecommunications and Co-Chair […]

By 2020, less than a year and a half away, an anticipated 20+ billion devices will likely be connected via the Internet of Things (IoT), creating incredible amounts of data […]

Engineering is just one of many professions that requires participation in continuing education programs in order to maintain a license. However, even if your particular line of work doesn’t require […]

The Grid Modernization Initiative (GMI) is a collaboration across the U.S. Department of Energy (DOE) to create the modern power grid of the future. It represents a comprehensive effort to […]

The Internet of Things (IoT) is ever expanding, with billions of touchpoints constantly requiring attention. Eventually, only cost-effective edge infrastructure will be able to keep up with IoT data processing. […]
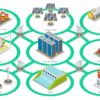
In 2016, the United States Department of Energy proposed an investment of $3.5 billion over the following decade to modernize our electric grid. Smart grid technology promises to better align energy […]

Thanks to the Internet of Things (IoT) more and more devices are connected, including homes, heating systems, fitness trackers, vehicles and more. Gartner projects that IoT devices will climb to […]

The Internet of Things (IoT), is a vast and growing universe of connected products ranging from fitness trackers and smart TVs to self-driving cars and virtual assistants. It has the […]
