Latest Posts

The Cyber Threats Lurking in Social Media
We often hear that we should be careful when choosing the comments, photos, and other media we share with our networks on social media. After all, what we post affects our reputation. But now there’s also a new worry. Did you know that your participation ...
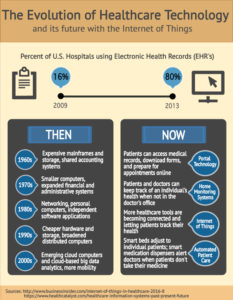
Infographic: Healthcare Technology and Internet of Things
The healthcare industry has seen a major shift in its use of technology over the past several decades. Protocol that used to rely on paper and pencil have now been replaced with computers and digital software. Aside from these differences within the hospital, such changes have also affected ...

Should you Hire an Ethical Hacker?
With cyber attacks on the rise, how can you ensure your organization’s digital work space is secure? More and more, companies are looking to train or hire an ethical hacker for help in finding and fixing security issues. Ethical hackers, also referred to as “white ...

Three Reasons Why Organizations Don’t Take Cyber Security Seriously Enough
The risk of cyber attack regularly increases in frequency and danger. Every day, it seems, there is another news article about the next attack, which is creating a great deal of concern in organizations large and small. Yet cyber security as a whole continues to be ...

How to Strengthen Your Organization’s Cyber Security
How prepared is your organization to manage a cyber attack? Do you need to strengthen cyber security for your organization? According to a recent report from ISACA, a professional association focused on IT governance, many security leaders anticipate a cyber attack on their organization in the ...

Four Internet of Things Companies to Watch
As the Internet of Things (IoT) continues to grow and pervade many areas of daily life, several companies have been quick to pursue this lucrative opportunity. According to Business Insider, below are four companies making notable, innovative contributions to the IoT field that will be worth watching in the days to come ...

Are Engineers Easy Targets for Cyber Criminals?
In a recent IEEE Spectrum Online article, Scott Borg, director of the U.S. Cyber Consequences Unit, was quoted as saying that the future of cyber security is in the hands of hardware engineers. Borg warned that “the people in this room are now moving into the crosshairs ...

What’s Next for Enterprise-Level Internet of Things?
The Internet of Things at an enterprise level needs to be driven by strong vision at the C-level, says Chris Penrose, president of AT&Ts Internet of Things organization. In a recent article in IOT Journal, he laid out some trends for 2017 that will drive ...

Securing the Internet of Things from Cyber Attack is Critical
The Internet of Things is transforming industries. Healthcare devices collect personal information and share it to help doctors make better healthcare decisions for patients. Logistics and manufacturing can improve efficiencies and identify potential problems quickly. And that’s just the beginning. Just about every industry can ...








